Bridging the gap Combining Cloud and On-Premise Security...
Read MoreBlog
Stay informed
Read our blog to stay well informed about cyber news and other valuable information.
Critical Boot Loader Vulnerability in Shim
Critical vulnerability in the Shim boot loader What...
Read MoreCybersecurity Trends 2024
Cybersecurity trends 2024 Intelligent & Resilient – Security...
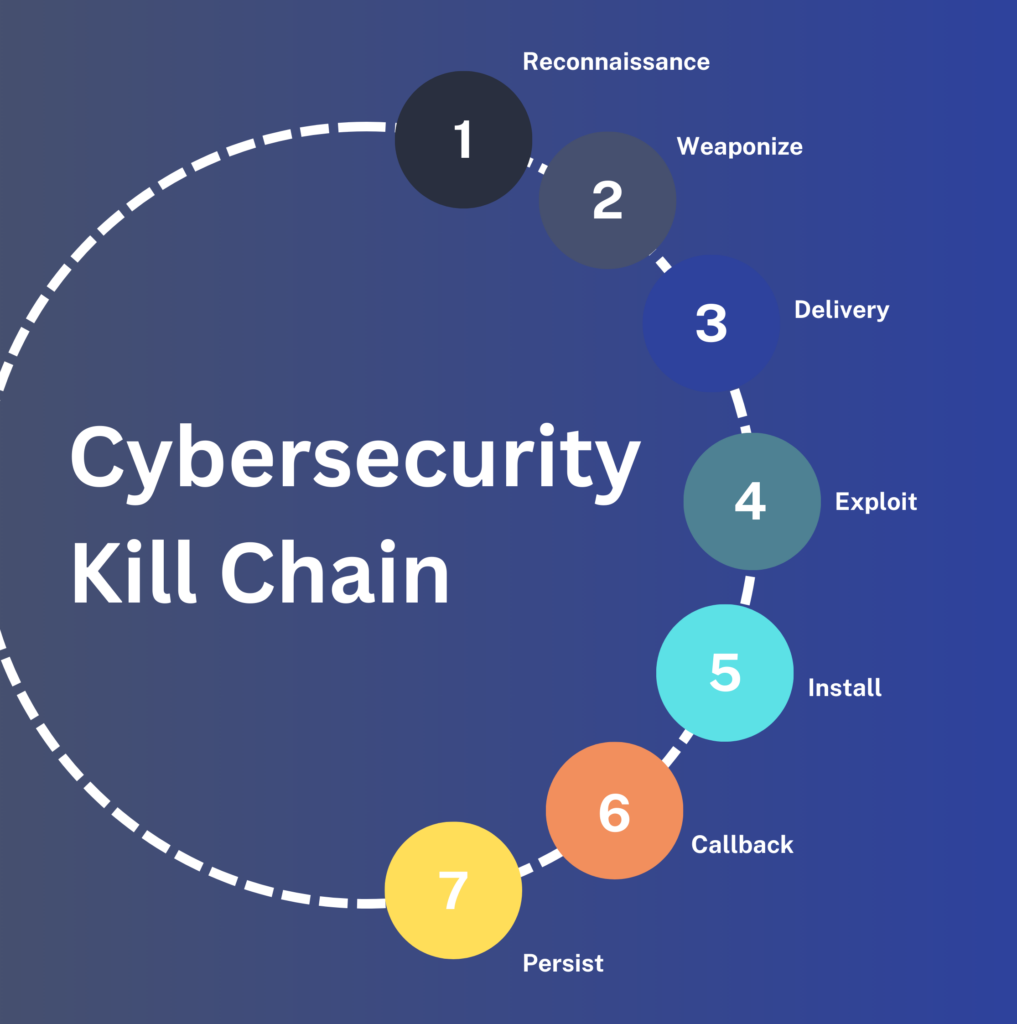
Read MoreCybersecurity Kill Chain
What is a Cybersecurity Kill Chain? understanding, detecting,...
Read MoreInternship at C4SAM
Internship @ C4SAM Find out what our interns...
Read MoreWhy should SMEs be interested in cybersecurity awareness
Why should anyone target us? Why should SMEs...
Read MoreMastering GRC in 2023
Mastering GRC in 2023 4 Essential Priorities to...
Read MoreTop 8 Prediction for Cybersecurity within the next 2
Top 8 Prediction for Cybersecurity within the next...
Read MorePart 2 – Why you should implement security processes
Why you should implement security processes in service...
Read MorePart 1 – Why you should implement security processes
Why you should implement security processes in service...
Read MoreSMBs are much more likely to be attacked
SMBs are much more likely to be attacked...
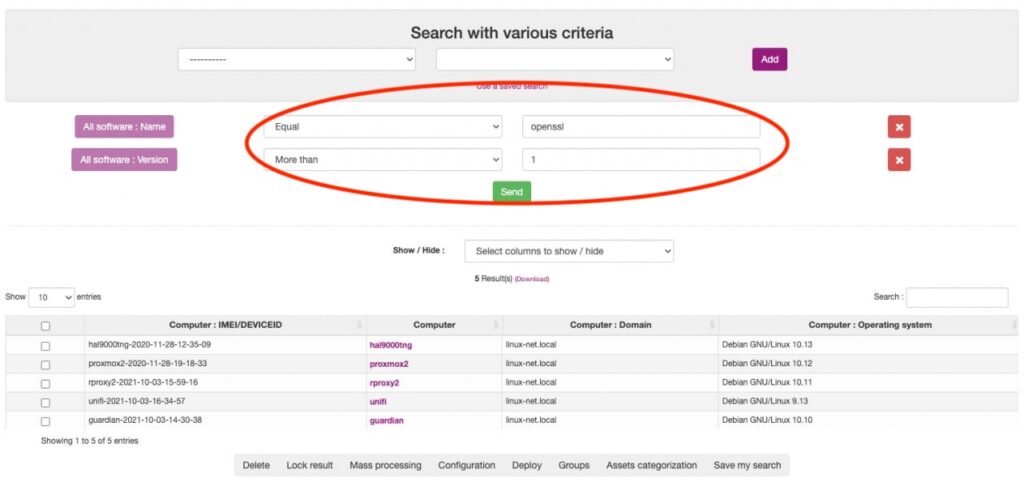
Read MoreZeroday Vulnerabiltity in OpenSSL
Zeroday vulnerabiltity in openssl – What to do?...
Read More4 Rules to help prevent, identify and limit the
4 Rules to help prevent, identify and limit...
Read MoreIKT Sicherheitskonferenz 2022
Besuchen sie uns auf der IKT Sicherheitskonferenz am...
Read MoreThe most dangerous Attacks of 2022
The most dangerous cyber Attacks of 2022 It’s...
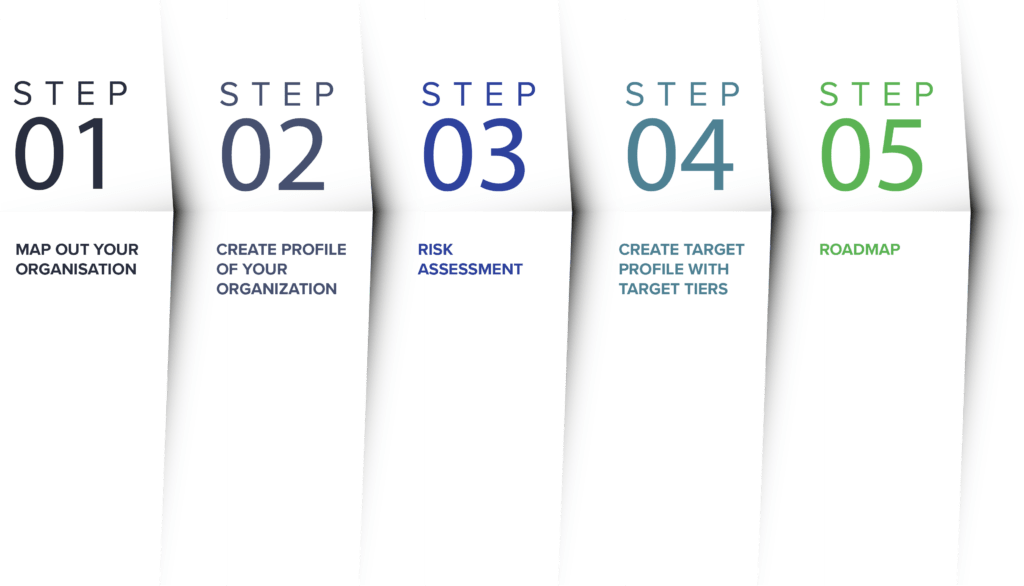
Read MoreA quick 5 step guide for everyone who is
A quick 5 step guide for everyone who...
Read More3 reasons why the NIST Framework is a great
3 reasons why the NIST Framework is a...
Read More