C4SAM
Technical Information
Find out more about the architecture und functions of our solution.
C4SAM 4-Stage Cycle
1. Identify
Risk Assessment | Compliance Assessment | Vulnerability Management | CMDB & Discovery Management | CSAM Asset Management
2. Monitor / Protect
Information Protection | File Integrity Monitoring | Team Password Management | Host Based Intrusion Detection | Data Security | Network IPS
3. Detect
Security Monitoring | Application Monitoring | System Monitoring | Network IDS | SIEM & Event Logging | Network Monitoring | File Integrity Monitoring
4. Respond
Automation Management | Incident Management | Alert & Rule Management
Architecture
Depending on the needs of the specific IT Infrastructure a company can have one or more minions, as well as one or more cockpits.
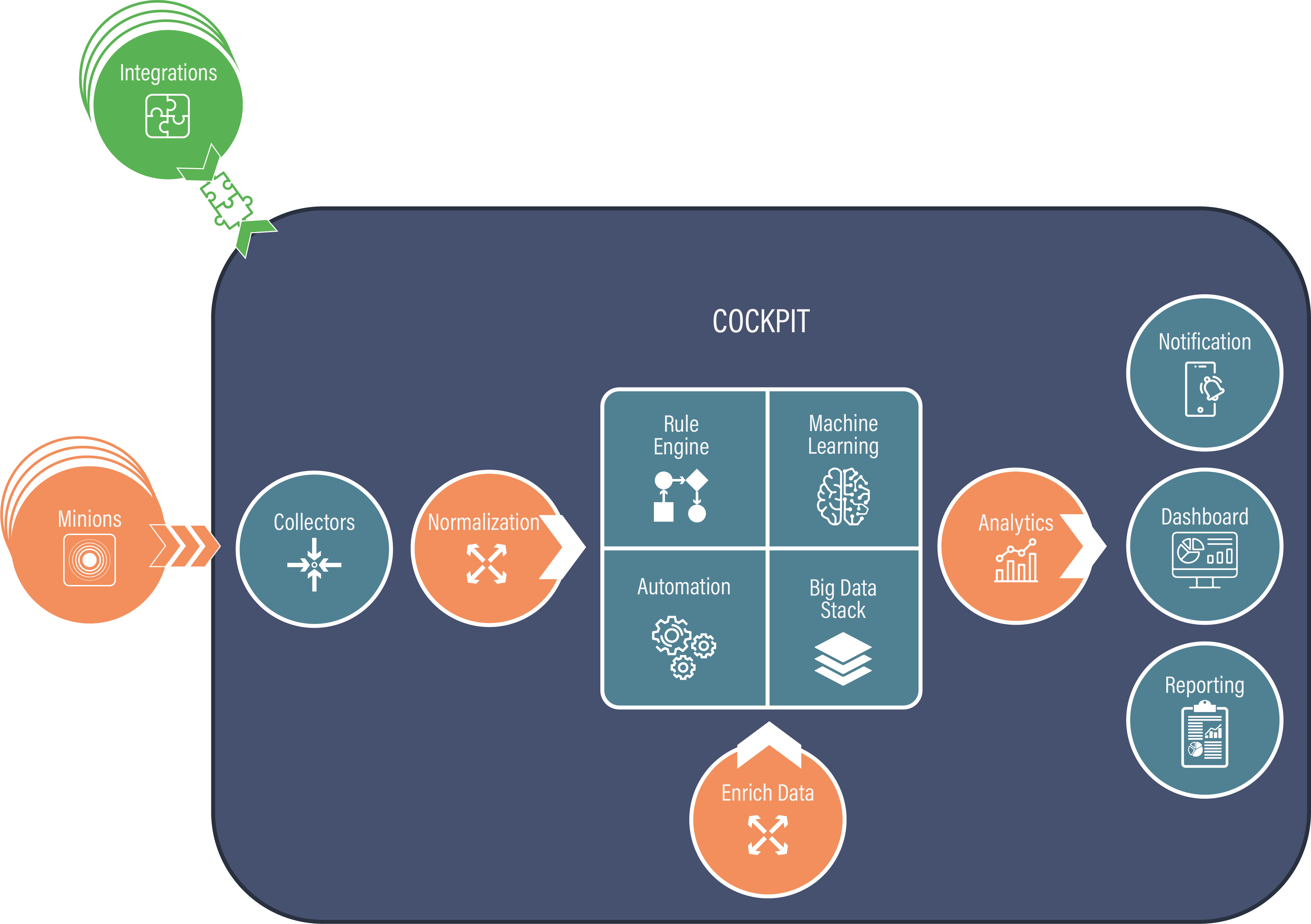
Topology
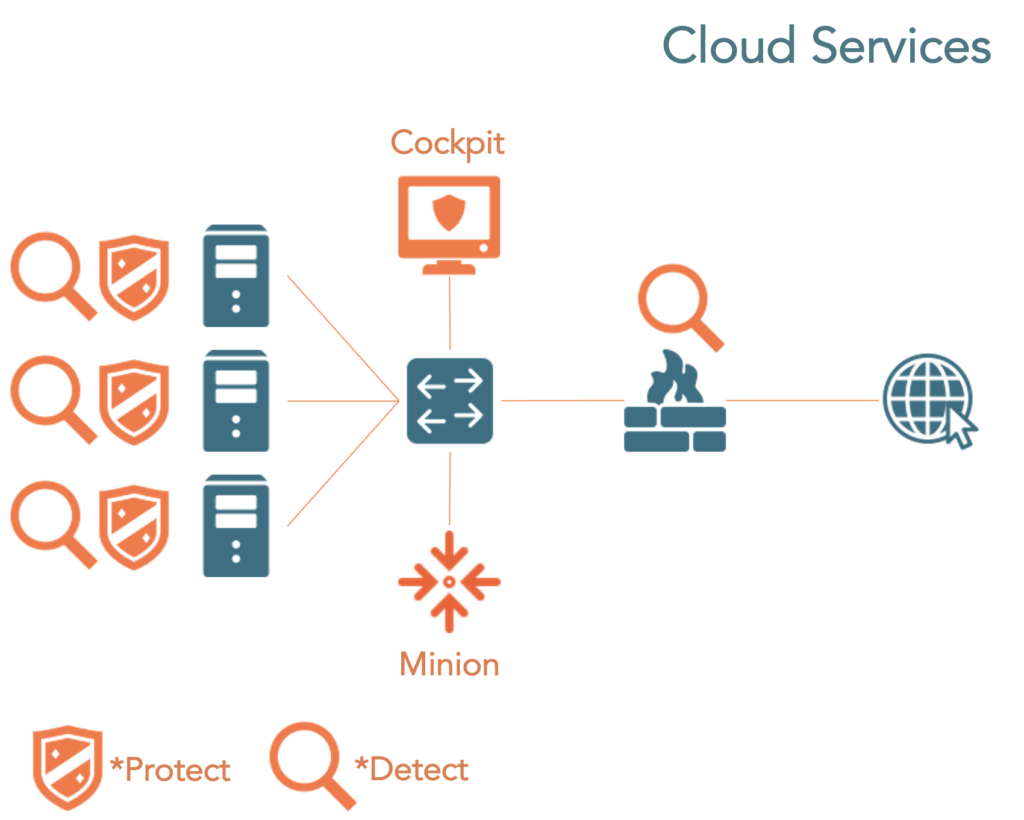
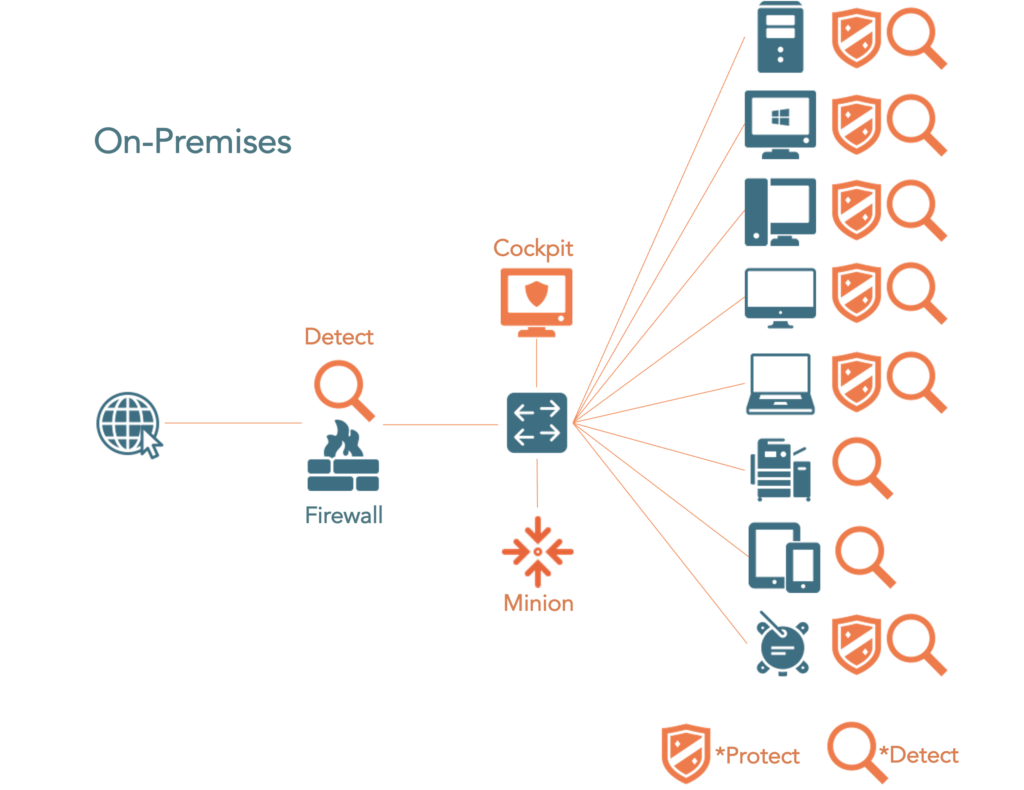
Our solution is available as cloud service or on-premises or as MSSP for our partners.
Cloud services can also be mixed with on-premises. Choose your favorite deployment.