CYPSec x C4SAM Strategische Partnerschaft zur Stärkung moderner Cyber-Resilienz C4SAM...
Mehr lesenZeroday vulnerabiltity in openssl - Was ist zu tun?
Wie Sie vielleicht alle gehört haben, hat OpenSSL Sicherheitsempfehlungen veröffentlicht, um zwei neue Schwachstellen zu beheben, CVE-2022-3602 und CVE-2022-3786, die OpenSSL-Versionen von 3.0.0 bis 3.0.6 betreffen.
Beide Sicherheitslücken können einen Denial-of-Service verursachen. Ihnen zufolge könnte ein Cyber-Bedrohungsakteur, der CVE-2022-3786 nutzt, eine böswillige E-Mail-Adresse erstellen, um vier von Angreifern kontrollierte Bytes auf dem Stapel zu überlaufen. Dieser Pufferüberlauf könnte zu einem Absturz führen, der einen Denial-of-Service (DDOS) oder möglicherweise eine Remote-Code-Ausführung (RCE) verursacht, wodurch sie die Kontrolle über ein betroffenes System übernehmen können.
Was ist DDOS?
DDoS (Distributed Denial of Service) sind böswillige Cyberangriffe, die von Cyberkriminellen eingesetzt werden, um einen Onlinedienst, eine Netzwerkressource oder einen Hostcomputer unzugänglich zu machen. Diese Vorfälle sind eng mit Botnets verbunden, bei denen Hacker die Kontrolle über Tausende von mit dem Internet verbundenen Geräten übernehmen und dann in koordinierten Angriffen alle diese Geräte anweisen, gleichzeitig Anfragen an das Ziel zu senden.
Was ist RCE?
Diese Vorfälle sind eng mit Botnets verbunden, bei denen Hacker die Kontrolle über Tausende von mit dem Internet verbundenen Geräten übernehmen und dann in koordinierten Angriffen alle diese Geräte anweisen, gleichzeitig Anfragen an das Ziel zu senden. Diese Vorfälle sind eng mit Botnets verbunden, bei denen Hacker die Kontrolle über Tausende von mit dem Internet verbundenen Geräten übernehmen und dann in koordinierten Angriffen alle diese Geräte anweisen, gleichzeitig Anfragen an das Ziel zu senden.
Diese Vorfälle sind eng mit Botnets verbunden, bei denen Hacker die Kontrolle über Tausende von mit dem Internet verbundenen Geräten übernehmen und dann in koordinierten Angriffen alle diese Geräte anweisen, gleichzeitig Anfragen an das Ziel zu senden. Diese Vorfälle sind eng mit Botnets verbunden, bei denen Hacker die Kontrolle über Tausende von mit dem Internet verbundenen Geräten übernehmen und dann in koordinierten Angriffen alle diese Geräte anweisen, gleichzeitig Anfragen an das Ziel zu senden.
Diese Vorfälle sind eng mit Botnets verbunden, bei denen Hacker die Kontrolle über Tausende von mit dem Internet verbundenen Geräten übernehmen und dann in koordinierten Angriffen alle diese Geräte anweisen, gleichzeitig Anfragen an das Ziel zu senden.
Da es keinen Patch oder Workaround gibt, müssen CIOs oder CSOs von Unternehmen laut DSGVO sofort alle Systeme, die von dieser Schwachstelle betroffen sind, offline nehmen.
Aber woher wissen Sie, welche Systeme betroffen sind?
Fragen Sie c4sam 42
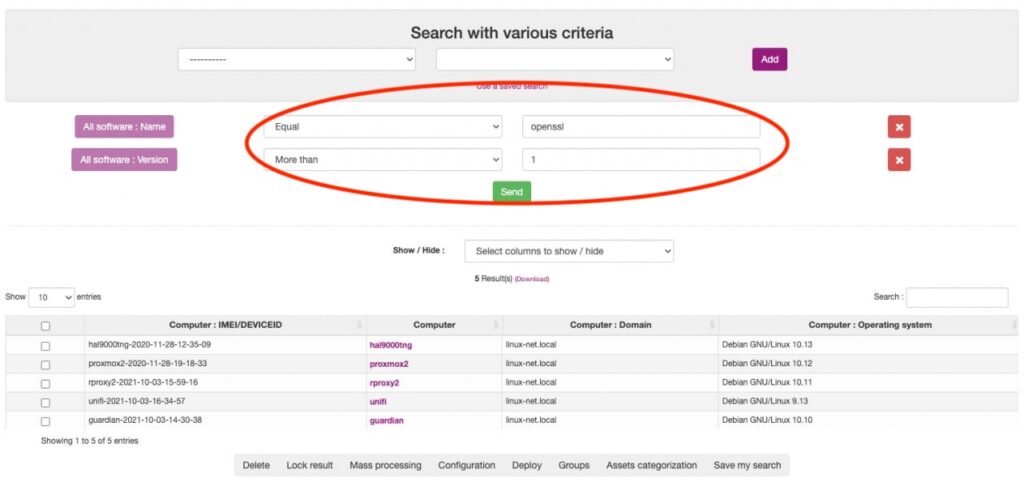
Durch eine automatisierte Bestandsidentifikation, die mit unserer Lösung einfach durchgeführt werden kann.
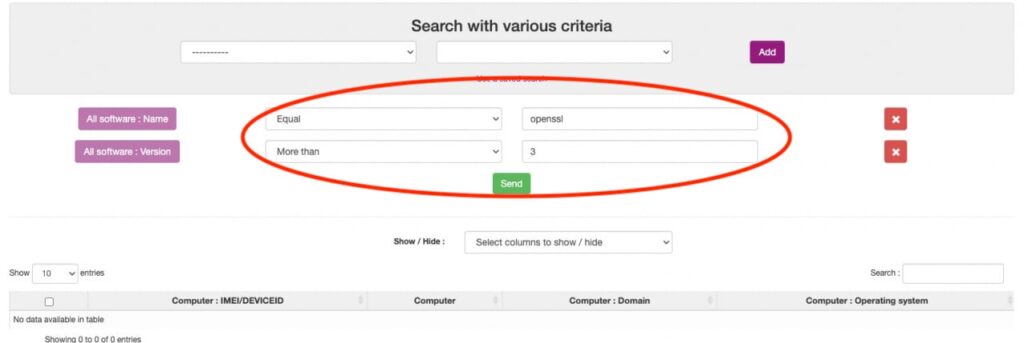
Smart filter – installierte Versionen < 3.xxx sind nicht betroffen.
Weitere Blog Posts
Überbrückung der Lücke: Kombination von Cloud- und On-Premise-Sicherheit mit C4SAM
Überbrückung der Kluft Kombination von Cloud- und On-Premise-Sicherheit mit C4SAM...
Mehr lesenKritische Bootloader-Schwachstelle in Shim
Kritische Sicherheitslücke im Shim-Bootloader Was ist zu tun? Eine kritische...
Mehr lesenCybersecurity Trends 2024
Cybersecurity-Trends 2024 Intelligent und widerstandsfähig – Sicherheit durch Automatisierung In...
Mehr lesenCybersecurity Kill Chain
Was ist eine Cybersecurity Kill Chain? Verständnis, Erkennung und Verhütung...
Mehr lesenWhy should SMEs care about cybersecurity?
Warum sollte uns jemand ins Visier nehmen? Warum sollten sich...
Mehr lesenGRC im Jahre 2023 meistern
GRC im Jahre 2023 meistern 4 wesentliche Prioritäten zur Sicherung...
Mehr lesen